Blog
Secure Your Remote Workforce With Zero Trust Security
04/01/2021


Zero Trust is an IT security framework based on an organisation assuming that any users or devices inside or outside of their network are unsecure until they have been fully verified. Every access request is authenticated, authorised and encrypted before access is granted to the chosen network. In short, it encourages us to ‘never trust, always verify’.
Zero Trust allows restricted access to data, applications and devices only to those who require admittance in order to perform their job role. This is known as 'least privilege access'.

Today’s organisations require an IT security approach that can adapt to the complexities of the new modern workplace. Companies no longer have all their data located in one place within the secure parameters of a head office. As a result, this increases the difficulty of deploying centrally controlled IT security to ensure remote workers, digital devices and data are protected against malicious threats no matter their location.
The Zero Trust IT security model offers peace of mind that users can access their data and networks securely regardless of application or user location when required. This reduces the security threat posed by internal misuse of data as well as the risks posed should one of your team’s accounts become compromised.
Zero Trust is now gaining momentum as a model for the long-term modernisation of network security and the prevention of data breaches. In a recent survey, 72% of businesses planned to assess or implement Zero Trust capabilities in some capacity in 2020 to help mitigate growing cyber risks.1
Implementing a Zero Trust framework takes time, requires collaboration across your organisation and with your IT solutions provider. Your strategy should include; a final infrastructure plan, a step-by-step guide of how to reach your end goal, and plans for your existing IT security to remain functional throughout a phased transition.

A Zero Trust approach should extend across your entire digital network ‘as an integrated philosophy and end-to-end strategy’. To achieve this there are six key pillars that support implementing Zero Trust that take a holistic approach to help fully defend your organisation from malicious threats. Here are the six key pillars as defined by Microsoft.3,4
Identities
Identities can include people, services or devices. All identities should be verified with strong authentication. This should ensure access is compliant and is a typical request for that identity. The request should also follow your least privilege access principles.
Devices
All devices accessing your networks and data should be visible. The variation of devices will offer a large attack surface area for cybercriminals to take advantage of. For this reason, devices should be continually monitored with regular software updates, allowing continued device health and compliance.
Applications
These can be made up of on-premise or modern SaaS (Software as a Service) applications. You should have controls in place to discover shadow IT, ensure appropriate in-app permissions, access based on real-time analytics, monitoring for suspect behaviour, control of user actions and the validation of configurations.
Data
Data should be classified, labelled, encrypted and restricted, allowing it to be protected wherever it is stored or required to travel internally or externally.
Infrastructure
Employ real-time threat detection that can detect attacks or anomalies and automatically block and flag any risks. Implementing least privilege access principles can further protect your organisation.
Networks
To stop attackers from moving easily across your networks, they should be segmented. Real-time threat protection, end-to-end encryption, monitoring, policies and analytics should be deployed to further protect your data.
Below is a diagram that illustrates how the six pillars of Zero Trust security holistically help to protect an organisation’s networks and data.
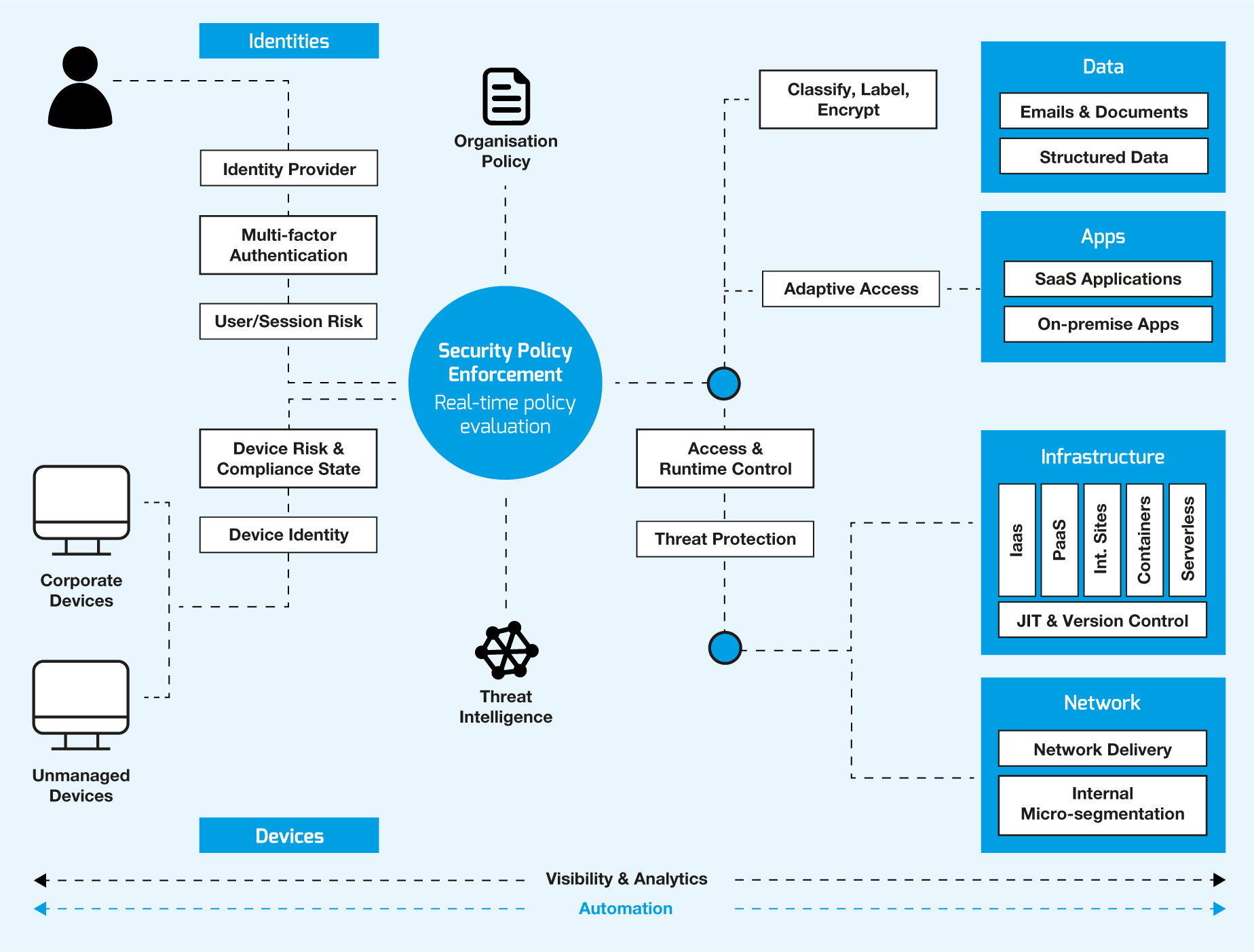

Not every Zero Trust model is the same, each plan is as unique as your business. Every organisation will have varying requirements, existing technology and available resources that should be taken into account. Our helpful team of IT experts can evaluate your IT security helping to build a phased plan that works towards fully implementing Zero Trust.
To start your Zero Trust journey you can book a free 30-minute review appointment here or call us on 01326 379 497 and speak to our friendly sales team.
Sources
Share
Call Me Back
I would like to discuss NCI Services & Support

Comments
Leave a comment below