Blog
Social Engineering: Could You Spot a Potential Attack?
26/06/2023
Social engineering attacks are currently one of the biggest cyber threats that small and medium organisations face, and attacks are skyrocketing at an alarming rate. Businesses such as Mailchimp, Linus Tech Tips and LastPass have recently made headline news by falling afoul of unauthorised parties gaining access to their customer data through compromised individuals.
Read along as we investigate the murky world of social engineering, explaining what it is, how it works, and the steps you can take to protect yourself.
What Is Social Engineering?
Social engineering refers to the techniques and psychological manipulation used by cybercriminals to exploit human error for financial gain. Using these methods, they can trick users into making security mistakes that allow them to gain access to your data and networks. Social engineering doesn’t just take place online. It happens in various forms, including vishing (phone), phishing (email), smishing (text), social media, mail, shoulder surfing and other methods of direct contact.
Socially engineered attacks cause devastating effects beyond the initial user targeted; your organisation may experience financial and reputational damage along with a drop in productivity. In many cases it can take months to realise that you’ve been a victim of a data breach and by then a huge amount of damage could have been done.
Did You Know?
 |
 |
 |
|
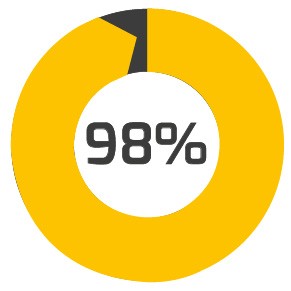
98% of cyberattacks relied on social engineering in 2022 |
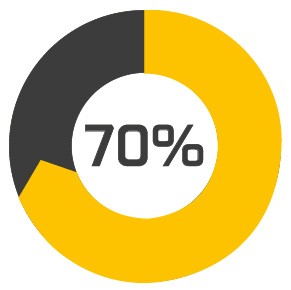
Over 70% of data breaches begin with social engineering |
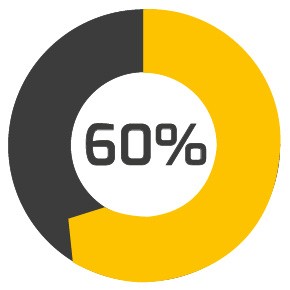
60% of small companies will close within 6 months after a cyber attack |
How Does Social Engineering Work?
Social engineering attacks are reliant on human error instead of threat actors taking advantage of security gaps in software and networks. The below infographic demonstrates the lifecycle of an attack:
 |
1. Investigation - Prepare ground for attack: - Identify victim(s) - Gather background information - Select attack method(s) |
 |
2. Hook - Deceiving the victim(s) to gain a foothold: - Engage target - Spin a story for the target - Take control of interaction |
 |
3. Play - Obtain information over time: - Expand foothold - Execute the attack on the target - Disrupt business or siphon data |
 |
4. Exit - Closing the interaction, without arousing suspicion: - Remove trace of malware - Cover tracks - Bring charade to a natural end |
Common Social Engineering Attack Techniques
As previously highlighted, social engineering can happen in various ways. Here are five of the most common social engineering attack methods used by cybercriminals:
> Baiting
Baiting involves appealing to a target’s curiosity for the attack to be successful. An attacker will leave a form of bait, such as a malware-infected USB, where it will be easily found. The intention is that curiosity will get the better of the intended victim and they will insert the USB into their computer, unwittingly installing malware onto their system. These attacks can also operate in the digital world in the form of ‘too-good-to-be-true’ ads that lead to malicious sites or downloads.
> Scareware
Scareware involves the attacker tricking the target into thinking that their device is already infected with malware using a method like an internet pop-up banner. The attacker will offer a solution via download to fix the fake issue. This is a deception, and the target will instead download malicious software or malware onto their device.
> Pretexting
Pretexting is a scam where an attacker lies to a target, pretending to need personal data to confirm their identity so they can perform a critical task. This kind of attack usually requires the cybercriminal to have some previous knowledge of the victim for them to gain additional information.
> Phishing
Phishing is one of the most popular social engineering attack methods, with scams normally carried out using bulk email or text. The attacker will pose as a trusted entity, such as a social media provider, bank, streaming platform or even a co-worker. The scam will create a sense of urgency or curiosity that will encourage the victim to reveal sensitive data, such as usernames, passwords, or financial details, by clicking on a link or downloading a malicious attachment.
> Spear Phishing
Although like phishing, spear phishing focuses the attack on a specific individual or organisation. The attacker will research the intended victim and tailor the scam email according to that person’s attributes, job role, and contacts, so it is not easily detected. An example scenario would be an attacker posing as your human resources team asking you to click on a link for an update on holiday entitlement.
How to Spot the Signs of a Social Engineering Attack
The below infographic highlights how you can spot the red flags of a potential phishing attack using email:
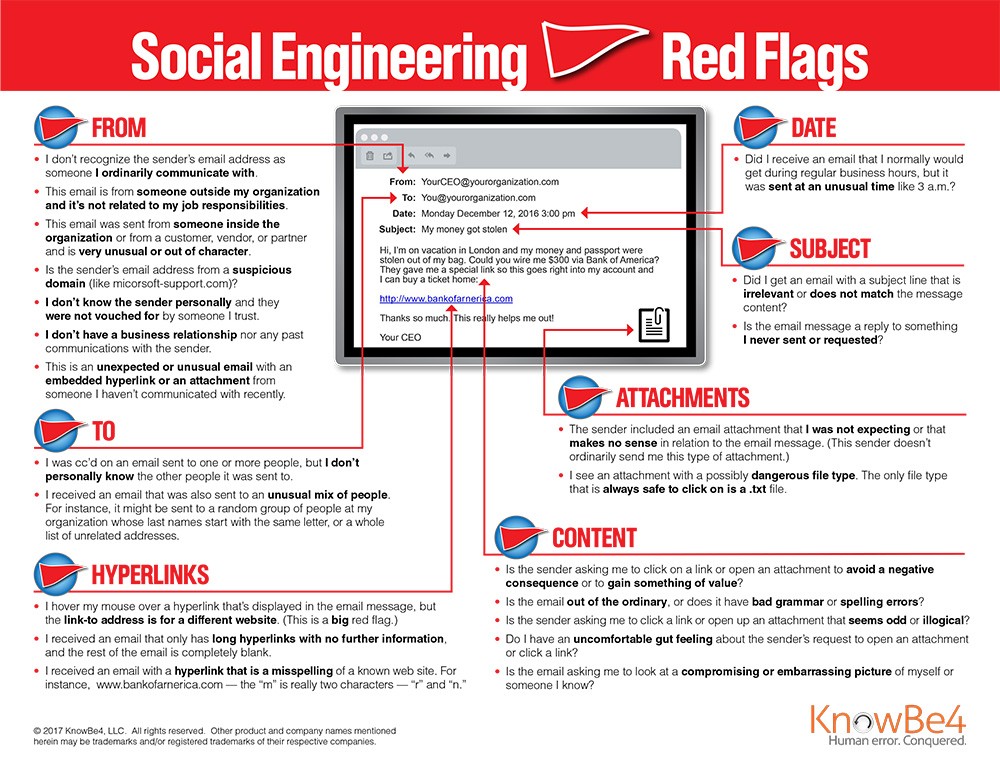
Download: 22 Social Engineering Red Flags PDF
How you can Prevent a Social Engineering Attack
Many organisations are unsure of how to protect themselves and their users from social engineering. We recommend taking the following steps to help protect against falling victim to an attack:
- Implement Secure Email Gateway and Web Gateways that offer URL filtering.
- Ensure your endpoints (digital devices) and Web Gateway have next-gen security layers that are regularly updated.
- Make sure your endpoints regularly receive security patches and updates for operating systems and apps such as Microsoft 365.
- Implement multi-factor authentication, especially for users who handle sensitive information.
- Develop internal security policies and incident response plans, paying special attention to financial transactions to help prevent CEO fraud.
- Check your firewall configuration, ensuring no criminal network traffic can slip through.
- Educate your employees by implementing an organisation wide cybersecurity awareness training plan that includes frequent social engineering tests.
- Ensure you have a robust backup and recovery process in place for your data.
- Create strong passwords that are difficult to guess.
- Encourage employees to think about their digital footprint and what information they share online.
The Last Line of Defence Against Social Engineering is YOU!
Don’t let human error be the weak link in your organisation’s cybersecurity strategy! One of the best ways to ensure your organisation doesn’t suffer the effects of human error is to implement a company-wide cybersecurity awareness training plan.
Serving Cornwall, Devon and the South West, NCI Technologies offers modern automated cybersecurity awareness training that will continually educate your staff, helping to build a resilient and secure organisation.
For more information contact us today, alternatively book a Teams or in-person meeting with our friendly sales team.
Share

Comments
Leave a comment below