Blog
Five Strategies to Help Navigate the Challenges of MFA Fatigue
02/04/2024

In an age dominated by digital advancements and the constant need for heightened security measures, multi-factor authentication (MFA) has emerged as a reliable guardian against unauthorised access. While MFA without doubt fortifies our online defences, there is a growing concern that the need for users to frequently authenticate themselves is leading to issues with ‘MFA fatigue’. In this blog, we will explore the concept, its implications, and how organisations and individuals can navigate this issue without compromising the security of their networks and data.
Did You Know?
|
|
 |
 |
|
Microsoft witnessed more than 382,000 attacks due to MFA fatigue1 |
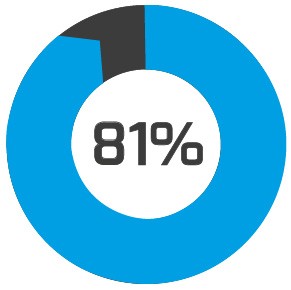
81% of data breaches occur because of weak passwords2 |
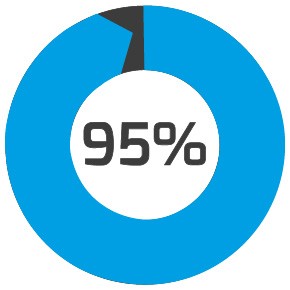
95% of cyberattacks are due to human error3 |
Understanding MFA Fatigue
MFA is an authentication method where the user is granted access to an application or website after identifying themselves with two or more additional verification factors. Usually, this includes a combination of passwords, biometrics, and one-time passcodes. While MFA significantly enhances security compared to just using a password, users can find the requirement to constantly verify themselves intrusive and tiresome.
The Implications of MFA Fatigue
> Decreased Productivity
Excessive MFA prompts can easily disrupt user workflows. Users may experience delays in accessing accounts, systems, and data, leading to a decline in productivity as they spend more time authenticating access. As a result, users may become resistant to adopting new technologies and consistently using MFA, leading to non-compliance with security policies.
> Security Risks
Fatigued users might be tempted to use simpler, less secure passwords or decide to disable MFA altogether to streamline their login process, inadvertently exposing systems and data to security vulnerabilities.
> User Frustration
Continuous prompts for additional verification may result in user frustration and a negative perception of cybersecurity measures. Users experiencing these issues may generate more IT support requests due to forgotten credentials or challenges related to MFA, placing an additional strain on your IT resources.
> Falling Victim to an MFA Fatigue Attack
Malicious actors may exploit MFA by focusing on users experiencing fatigue from the constant need for verification. MFA attacks, a form of social engineering, target the significant cybersecurity vulnerability of human error.
Initially, attackers acquire a user's login credentials and subsequently inundate them with a continuous stream of MFA notifications. The goal is to deceive users into unwittingly approving a fraudulent login attempt, providing the attacker with unauthorised access to their account. If this approach proves unsuccessful, the attacker may resort to direct contact with the user, posing as a trusted entity and requesting approval of the MFA prompt.
In 2022, Uber experienced a notable incident that serves as an example of a successful MFA attack. You can find out more about the incident here.
Strategies for Mitigating MFA Fatigue
> Educate Your Users
Organisations should provide clear and concise information about the importance of using MFA and how it contributes to your organisation’s overall cybersecurity. If users understand its importance, their cooperation in its use can be assured.
> Adaptive Authentication
Using adaptive authentication systems where user identity and authorisation levels are assessed based on location, device status and end-user behaviour can help tailor the MFA experience based on the perceived level of threat.
> Biometric Enhancements
Including biometric authentication methods, such as fingerprint or facial recognition, can enhance security without requiring users to remember complex passwords.
> Single Sign-on (SSO)
The integration of Single Sign-on solutions can reduce the frequency of authentication prompts, allowing users to access systems with a single login. SSO allows users to use one set of login credentials to access multiple apps. This can be an advantage in reducing MFA fatigue amongst users but if unauthorised access is gained, attackers can access more than one application. As a result, SSO should always be used in conjunction with MFA to improve security.
> Enhanced Cybersecurity Training
Consistent cybersecurity training sessions will help remind users on how to securely manage their credentials along with the importance of using MFA to help protect your organisation’s networks and data.
Beat the Threat of MFA Fatigue and Bolster Your IT Security Posture
MFA fatigue should be a real concern for businesses. By adopting a holistic approach that combines advanced authentication methods, user education and adaptive technologies, organisations can maintain a balance between robust cybersecurity measures and a user-friendly experience. As we continue to navigate the ever-changing digital world, the key lies in evolving our security practices to meet the requirement for increased security protection and user convenience.
Catering to businesses and schools across Cornwall, Devon, and the South West, NCI Technologies provides a modern and proactive stance on cybersecurity. Our team of IT experts are readily available to assist your organisation, employing a customised approach to IT security aimed at safeguarding your operations against everchanging cyber threats. Our goal is to ensure that you can focus on running your organisation, whilst reducing the risk from cyber threats and downtime.
Find out more on how we can support your organisation by contacting us or by scheduling a Teams or in-person meeting with our friendly sales team.
Share


Comments
Leave a comment below